The cybersecurity community has long lived by a simple principle: Don’t collect more data than you can protect. But ID…
Active Directory sites are designed to optimize network performance across geographically separated organizations by managing replication and authentication across multiple…
Security researchers have uncovered a dangerous attack vector targeting Active Directory Sites, a critical yet often overlooked component of enterprise…
Sekoia, a cyber threat detection and response specialist, has released details on a widespread and ongoing cybercrime operation that first…
Some of the world’s most widely used open-weight generative AI (GenAI) services are profoundly susceptible to so-called “multi-turn” prompt injection…
Cisco warned this week that two vulnerabilities, which have been used in zero-day attacks, are now being exploited to force ASA and…
Microsoft’s upcoming Teams update, set for targeted releases in early November 2025 and worldwide by January 2026, will allow users…
LockBit has remained one of the most dominant ransomware-as-a-service (RaaS) groups in the world since its emergence as ABCD ransomware…
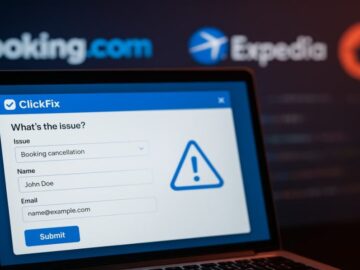
Early on in 2025, I described how criminals used fake CAPTCHA sites and a clipboard hijacker to provide instructions for…
A newly disclosed security flaw in the Amazon WorkSpaces client for Linux has raised serious concerns across organizations relying on AWS virtual desktop infrastructure. The…
Before JSON Web Tokens (JWTs) became popular in today’s app development landscape, web applications predominantly used server-side sessions, which presented…
LockBit 5.0 made its debut in late September 2025, marking a significant upgrade for one of the most notorious ransomware-as-a-service…