LinkedIn Used by Scammers to Distribute Malware: A New Threat LinkedIn, a leading platform for professional networking, is now being…
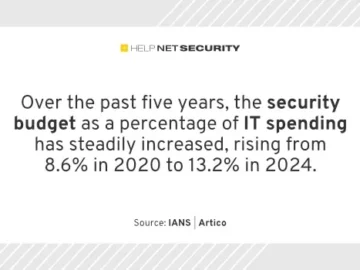
Amidst global economic and geopolitical uncertainty, markets are jittery, companies are spending frugally, and investors remain cautious, according to IANS…
Sep 09, 2024Ravie LakshmananCyber Attack / Threat Intelligence A previously undocumented threat actor with likely ties to Chinese-speaking groups has…
IBM has revealed several severe vulnerabilities within its webMethods Integration Server, a platform widely utilized for integration and API management….
Australia Post is paring back the number of technology service providers it works with, unveiling a panel of five that…
Progress Software fixed a maximum severity flaw in LoadMaster Pierluigi Paganini September 09, 2024 Progress Software released an emergency to…
Bitcoin ATMs (BTMs) have emerged as a convenient tool for cryptocurrency transactions, but they have also become a hotbed for…
In today’s digital era, protecting healthcare data from cyber attacks is more crucial than ever. The healthcare sector, rich with…
In this Help Net Security interview, Umaimah Khan, CEO of Opal Security, shares her insights on implementing the Principle of…
Last week on Malwarebytes Labs: Last week on ThreatDown: Stay safe! Our business solutions remove all remnants of ransomware and…
Sep 09, 2024Ravie LakshmananMobile Security / Cryptocurrency Android device users in South Korea have emerged as a target of a…
While software-defined wide area networks (SD-WANs) evolved from the need to provide branch offices with access to corporate applications and…