Park’N Fly is warning that a data breach exposed the personal and account information of 1 million customers in Canada…
The eight Android and iOS apps fail to adequately protect user data, which transmits sensitive information, such as device details,…
The United States Supreme Court recently stymied recent cyber security regulations and plans. To fight the proliferation of cyber security…
Hackers relentlessly probe your organization’s digital defenses, hunting for the slightest vulnerability to exploit. And while penetration testing serves as…
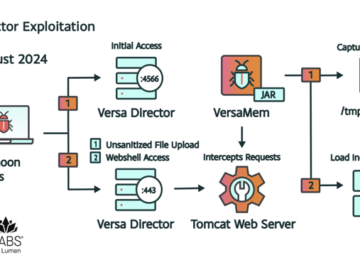
Malicious hackers are exploiting a zero-day vulnerability in Versa Director, a software product used by many Internet and IT service…
The China-nexus cyber espionage group tracked as Volt Typhoon has been attributed with moderate confidence to the zero-day exploitation of…
In the modern workplace, the proliferation of endpoints has significantly expanded the attack surface, presenting new security challenges for organisations….
A massive QR code phishing campaign abused Microsoft Sway, a cloud-based tool for creating online presentations, to host landing pages…
In April 2024, the FBI warned about a new type of smishing scam. Smishing is the term we use for…
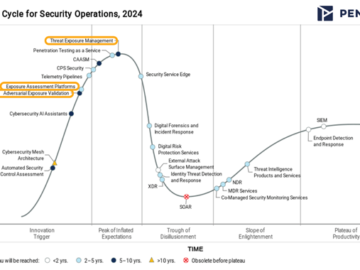
Want to know what’s the latest and greatest in SecOps for 2024? Gartner’s recently released Hype Cycle for Security Operations…
Cisco has announced its intent to acquire Robust Intelligence, a leader in AI application security. This acquisition aligns with Cisco’s…
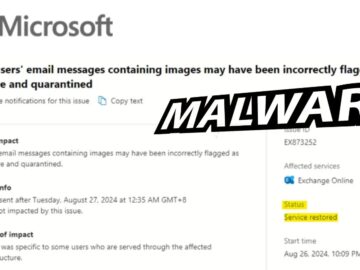
Microsoft 365 users have reported a troubling issue in which email messages containing images are incorrectly flagged as malware and…