Defending business against cyberattack Encryption of Data at Rest: The Cybersecurity Last Line of Defense In the ever-evolving landscape of…
27 Aug Most Ransomware Attacks Occur When Security Staff Are Asleep Posted at 08:46h in Blogs by Di Freeze This…
The Texas Dow Employees Credit Union (TDECU) has filed a data breach notification, reporting that the data of 500,474 people…
Denmark’s Chamber of Commerce, Dansk Erhverv, is fronting a national consortium of state and private organisations to launch a Danish…
Researchers have revealed that a critical security flaw in Microsoft 365 Copilot allowed attackers to exfiltrate sensitive user information through…
A security researcher revealed a critical vulnerability in Microsoft Copilot, a tool integrated into Microsoft 365, which allowed hackers to…
Researchers unmasked the notorious threat actor USDoD Pierluigi Paganini August 27, 2024 CrowdStrike researchers have identified the notorious hacker USDoD…
Argentine authorities have dismantled a sophisticated cryptocurrency operation based in Buenos Aires. The operation, which was allegedly connected to North…
TDECU reports a data breach affecting over 500,000 members due to a MOVEit vulnerability. Compromised data includes Social Security numbers…
Greasy Opal, based in the Czech Republic since 2009, is reportedly a Cyber Attack Enablement company that manufactures and markets…
Razr ransomware is exploiting PythonAnywhere to distribute and encrypt files with AES-256. ANY.RUN’s analysis reveals its behaviour, C2 communication, and…
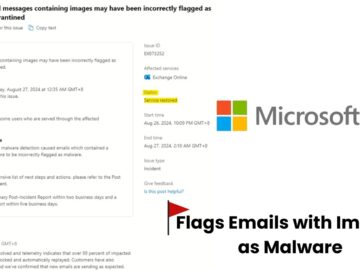
Microsoft 365 has acknowledged an issue affecting its Exchange Online service, where some users’ email messages containing images are being…