In this Help Net Security interview, Christos Tulumba, CISO at Veritas Technologies, discusses the key factors contributing to increased personal…
Access to timely and accurate threat intelligence is now core to security operations for many organizations. Today, it seems that…
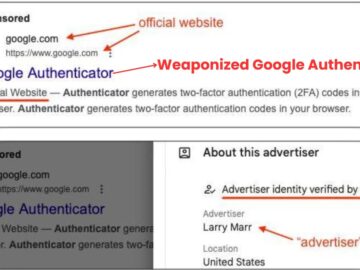
In recent days, threat actors have leveraged the popular Google Authenticator (a multi-factor authentication program) through Google ads, infecting devices…
The aviation industry has traditionally focused on physical security threats, but recent revelations about risks on Boeing‘s supply chain have…
Since February 2022, a highly advanced Android malware campaign has been specifically designed to attack one-time passwords (OTPs), which are…
Despite robust defenses, Cross-Site Scripting (XSS) remains a persistent web vulnerability, as its exploitation has become increasingly challenging. A recent…
Here’s a look at the most interesting products from the past month, featuring releases from: AttackIQ, AuditBoard, Black Kite, BlueVoyant,…
Image: Midjourney A malicious fraud campaign dubbed “ERIAKOS” promotes more than 600 fake web shops through Facebook advertisements to steal…
As cyberattacks on healthcare organizations surge, several state-level lawmakers are pushing back against what they see as excessive class-action lawsuits…
Researchers uncovered a critical operational security (OPSEC) failure by the Medusa Ransomware Group, allowing them to access the group’s cloud…
A new Android malware that researchers call ‘BingoMod’ can wipe devices after successfully stealing money from the victims’ bank accounts using…
The Mayor of London has launched a trial of the London Privacy Register, which aims to provide greater openness around…