The Police Digital Service (PDS) has lost another director in the form of ex-Accenture UK policing and justice lead Allan…
California’s Department of Motor Vehicles (DMV) has digitised 42 million car titles using blockchain technology in a bid to detect…
DigiCert urges critical infrastructure operators to request a delay if they cannot reissue their certificates, as required by an ongoing…
Software company Pegasystems has persuaded a court to throw out a decision by a jury to award rival Appian $2bn…
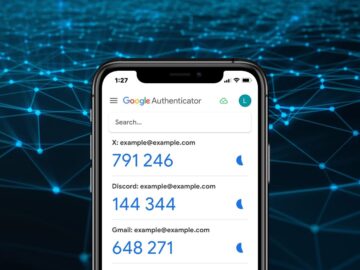
Google has fallen victim to its own ad platform, allowing threat actors to create fake Google Authenticator ads that push…
Google has introduced several measures to address this threat, including Safe Browsing download protection in Chrome, Device Bound Session Credentials,…
A coalition of financial services institutions and communications service providers, convened by consumer advocacy organisation Which?, have called on the…
Tl;DR; An OAuth misconfiguration was discovered in the redirect_uri parameter at the target’s OAuth IDP at https://app.target.com/oauth/authorize, which allowed attackers…
CISA and the FBI said today that Distributed Denial of Service (DDoS) attacks targeting election infrastructure will, at most, hinder…
Protect your data from cyber threats: Learn about RedLine, Vidar, and FormBook infostealers, their tactics, and how ANY.RUN’s sandbox helps…
Jul 31, 2024Ravie LakshmananCyber Espionage / Threat Intelligence Companies in Russia and Moldova have been the target of a phishing…
The CyberUp Campaign, a group calling for urgent reform to the Computer Misuse Act of 1990, has launched a fresh…