Microsoft has issued a statement apologizing for a recent IT outage, which they attribute to a DDoS (Distributed Denial of…
Reserve Bank of India (RBI), the country’s apex financial institution, has issued new directions to bolster cybersecurity and resilience of…
In the escalating world of cybercrime, ransomware attacks have become a pervasive threat, affecting businesses of all sizes and industries….
In this Help Net Security interview, Konrad Niemiec, CEO and Founder of Lekko, discusses the benefits of dynamic configuration in…
Former Uber CISO Joe Sullivan, who was convicted for attempting to cover up a data breach Uber suffered in 2016,…
Jul 31, 2024Ravie LakshmananPrivacy / Social Media Meta, the parent company of Facebook, Instagram, and WhatsApp, agreed to a record…
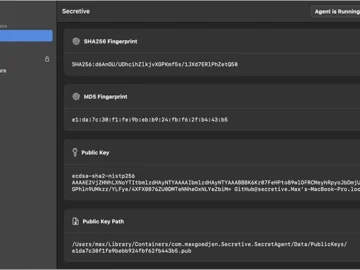
Secretive is an open-source, user-friendly app designed to store and manage SSH keys within the Secure Enclave. Typically, SSH keys…
Cybersecurity firm Zscaler has revealed that the Dark Angels ransomware group received an unprecedented $75 million ransom payment from a…
Cloud Security Architect Precisely | United Kingdom | Remote – View job details As a Cloud Security Architect, you will…
Western Sydney University has revealed that attackers had access to its Isilon storage infrastructure and 580TB of data for over…
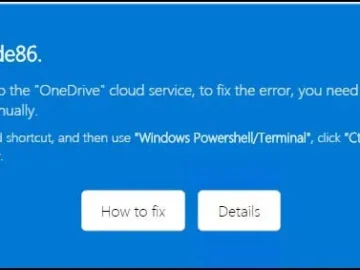
A new phishing campaign targeting Microsoft OneDrive users has been observed, employing social engineering tactics to trick victims into executing…
The U.S. Customs and Border Protection (CBP) agency has released a guide detailing how travelers can opt out of biometric…