24 Aug Smart Homes Pose Security Risks. How To Protect Your Devices. Posted at 09:37h in Blogs by Di Freeze…
Navigating the complex web of compliance in the AI era is a formidable challenge, and aligning your organization with existing…
Qilin ransomware is evolving, now targeting Google Chrome credentials. Learn how this new tactic expands their attack arsenal and how…
A new variant of Copybara, an Android malware family, has been detected to be active since November 2023 spreading through…
The United States Defense Department has ideas about a dramatic strategy for defending Taiwan against a Chinese military offensive that…
Cybersecurity analysts at Mandiant recently identified a stealthy memory malware dubbed “PEAKLIGHT.” A Stealth memory malware is often referred to…
Global geopolitical tensions are as bad as they’ve been in a long time. In this context, cyber warfare threatens our…
Aug 24, 2024Ravie LakshmananElection Security / Threat Intelligence Meta Platforms on Friday became the latest company after Microsoft, Google, and…
Aug 24, 2024Ravie LakshmananVulnerability / Government Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has placed a security flaw…
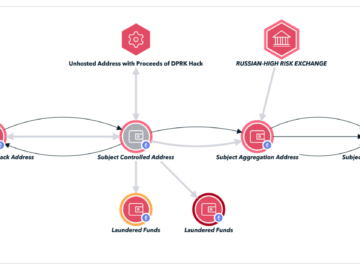
Russian national arrested in Argentina for laundering money of crooks and Lazarus APT Pierluigi Paganini August 24, 2024 A Russian…
The National Security Agency (NSA) has released the Best Practices for Event Logging and Threat Detection across cloud services, enterprise…
The U.S. Department of Justice has filed a lawsuit against the Georgia Institute of Technology – better known as Georgia…