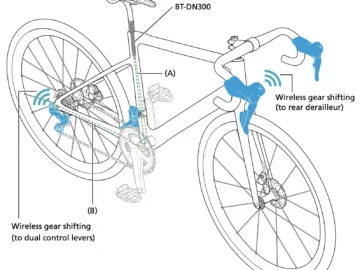
Researchers have recently uncovered vulnerabilities in the popular Shimano Di2 electronic gear-shifting system, raising concerns about the security of these…
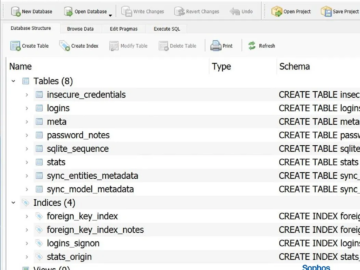
Qilin ransomware steals credentials stored in Google Chrome Pierluigi Paganini August 23, 2024 Sophos researchers investigated a Qilin ransomware breach…
Image: Midjourney The American Radio Relay League (ARRL) confirmed it paid a $1 million ransom to obtain a decryptor to…
As the world of software development accelerates, the need to secure applications from the earliest stages of development has become…
Some scammers have the morals of an alley cat. But some sink even lower. Over the last few months, Malwarebytes…
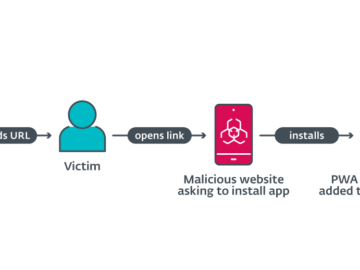
Phishing attacks target mobile users via progressive web applications (PWA) Pierluigi Paganini August 23, 2024 Cybercriminals use progressive web applications (PWA)…
Microsoft has provided a workaround to temporarily fix a known issue that is blocking Linux from booting on dual-boot systems…
Forget Game of Thrones and House of The Dragon; the real battle for power is between cyber criminals and security…
Member of cybercrime group Karakurt charged in the US Pierluigi Paganini August 23, 2024 The Russian national Deniss Zolotarjovs has…
Microsoft has released a new Windows 10 22H2 beta (KB5041582) with memory leak and crash fixes for Insiders in the…
A wave of attacks that started in July 2024 rely on a less common technique called AppDomain Manager Injection, which can…
A critical remote code execution (RCE) vulnerability in Microsoft Edge has been discovered. It could allow attackers to take control…