The year is only halfway over, but the healthcare sector has already reported 280 cyber incidents. That’s a staggering 24%…
Cybersecurity researchers have uncovered a sophisticated phishing campaign leveraging the “Cheana Stealer” malware, which has been distributed via a VPN…
China-linked APT Velvet Ant exploited zero-day to compromise Cisco switches Pierluigi Paganini August 23, 2024 China-linked APT group Velvet Ant…
A member of a notorious Russian cybercrime group has been charged federally and appeared in U.S. District Court in Cincinnati…
I was thrilled to catch up with Horizon3.ai during Black Hat USA 2024. Most attackers don’t break in, they log…
Over time, Deep State has added more advanced features and quirks to the map. A toolbar in the bottom-left corner…
Cyber-Informed Engineering (CIE) is a new perspective on OT cyber risk – one that is being embraced by OT/engineering teams and…
To improve your online visibility, it’s crucial to stay updated on the ever-evolving strategies and developments in Search Engine Optimization…
New research by Team Cymru, a global leader in external threat intelligence and exposure management, reveals that 50% of organizations…
23 Aug Questions To Ask Your Cloud Service Provider About Their Cybersecurity Posted at 08:57h in Blogs by Di Freeze…
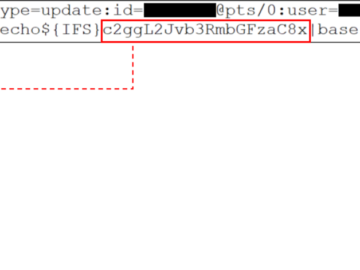
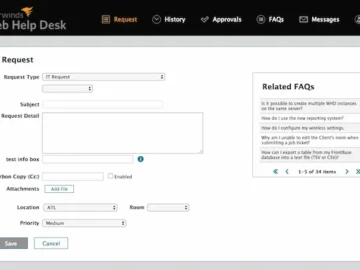
A week after SolarWinds released a fix for a critical code-injection-to-RCE vulnerability (CVE-2024-28986) in Web Help Desk (WHD), another patch…
Aug 23, 2024The Hacker NewsThreat Detection / Security Automation Let’s be honest. The world of cybersecurity feels like a constant…