INE Security, a global cybersecurity training and certification provider, recently launched initiatives with several higher education institutions in an ongoing…
In the first six months of 2024, Hiya flagged nearly 20 billion calls as suspected spam – more than 107…
A sophisticated China-linked cyber espionage group, known as Velvet Ant, has been discovered exploiting a zero-day vulnerability in Cisco NX-OS…
Despite the increasing number of cybersecurity tools available, attacks continue to succeed at an alarming rate. Studies show that more…
Vulnerability management has become more critical than ever as the global cost of cybercrime is projected to reach $10.5 trillion…
As security and identity management become increasingly more complex with 60% of breaches attributed to insider threats, compromising on access…
Here’s a look at the most interesting products from the past week, featuring releases from Entrust, Fortanix, McAfee, Own, RightCrowd,…
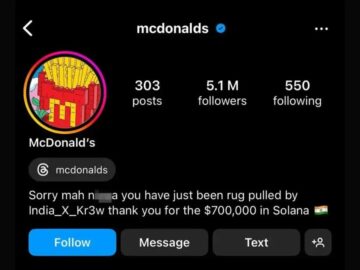
On August 21, 2024, McDonald’s official Instagram account was hacked, resulting in a cryptocurrency scam that made the hackers around…
Cisco has raised concerns about the recently adopted UN Convention Against Cybercrime, questioning its effectiveness in bringing about stricter international…
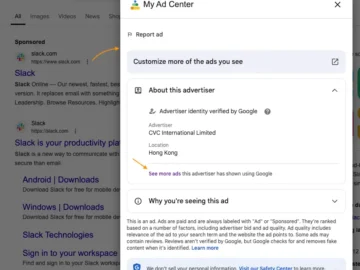
A sophisticated Slack malvertising campaign targeting users has been found exploiting Google search ads to deliver malware. This stealthy attack…
A cyberattack hit US oil giant Halliburton Pierluigi Paganini August 22, 2024 US oil giant Halliburton announced that it was…
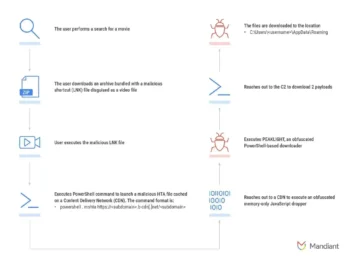
Cybersecurity experts have detailed a sophisticated new memory-only dropper linked to a multi-stage malware infection process. This dropper, dubbed PEAKLIGHT,…