C-suite executives face a unique challenge: aligning their priorities between driving technological innovation and ensuring business resilience while managing ever-evolving…
Nightfall AI’s research revealed that secrets like passwords and API keys were most often found in GitHub, with nearly 350…
ANZ Banking Group will put 3000 leaders through a new AI “immersion centre” at its Melbourne headquarters over the next…
NBN Co has now shifted “around 375,000” users to full fibre connections courtesy of its fibre-to-the-node and fibre-to-the-curb overbuild programs,…
While industrial VPN gateways such as Cosy+ play a crucial role in enabling secure remote access to critical operational technology…
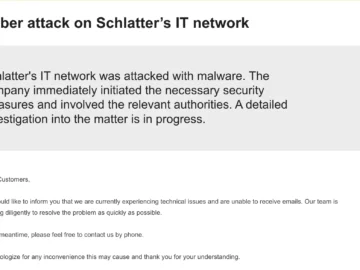
Switzerland-based Schlatter Industries announced that its IT network was compromised by a sophisticated malware attack on Friday. The company suspects…
Telstra is laying claim to having Australia’s largest deployment of Copilot for Microsoft 365, with the AI assistant to be…
European privacy advocate NOYB (None of Your Business) has filed nine GDPR complaints about X using the personal data from over…
The Department of Health and Aged Care has contracted Accenture to supply contractors into a large-scale digital transformation program underway…
The FBI announced on Monday that it seized the servers and websites of the Radar/Dispossessor ransomware operation following a joint…
US electric utilities sounded bullish on demand from data centres powering the artificial intelligence boom after striking several supply deals…
In a coordinated international takedown, the FBI, in collaboration with law enforcement agencies across the globe, has dismantled the infrastructure…