The C-suite is caught in an AI pressure cooker. On one side, boards and CEOs see the relentless headlines of…
ESET Research Threat Reports An overview of the activities of selected APT groups investigated and analyzed by ESET Research in…
China-linked threat actors have intensified their focus on influencing American governmental decision-making processes by targeting organizations involved in shaping international…
“What is recommended is that when something happens, they go to open the folder and the next day request the…
Russian-based threat actors are actively distributing a sophisticated Android Remote Access Trojan called “Fantasy Hub” via Telegram-based Malware-as-a-Service channels, marking…
Nov 07, 2025The Hacker NewsData Protection / Cloud Security Imagine this: Sarah from accounting gets what looks like a routine…
Chinese artificial intelligence systems are nearing levels of “frontier risks” similar to their US counterparts, according to a study. Recent…
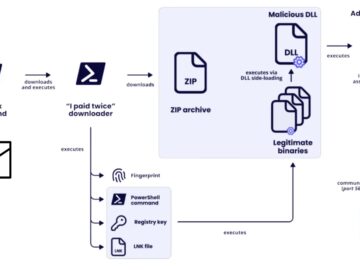
A dangerous two-stage malware threat, LeakyInjector and LeakyStealer, that targets cryptocurrency wallets and personal browser information explicitly. The malware duo…
Cybersecurity researchers have uncovered a sophisticated phishing campaign that exploits compromised hotel booking accounts to defraud travellers worldwide. The campaign,…
IT leaders need to weigh up the drive to adopt new, exciting innovation with the technical debt and mission-critical legacy…
In July 2025, a sophisticated hacker group known as Cavalry Werewolf executed a targeted campaign against Russian government institutions, compromising…
Datadog Security Research has uncovered a sophisticated supply chain attack targeting the npm ecosystem, involving 17 malicious packages across 23…