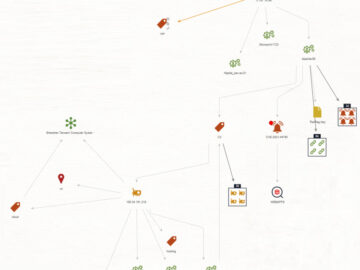
Evolution Mining Limited, a prominent global player in the gold mining industry, has reported a ransomware attack that impacted its…
Torrance, United States / California, August 12th, 2024, CyberNewsWire Criminal IP, an expanding Cyber Threat Intelligence (CTI) search engine from…
Torrance, United States / California, August 12th, 2024, CyberNewsWire Criminal IP, an expanding Cyber Threat Intelligence (CTI) search engine from…
Researchers have uncovered a sophisticated phishing marketplace, the ONNX Store, which provides cybercriminals with advanced tools to hijack Microsoft 365…
Hackers attack AWS as it hosts a vast number of high-value targets, including sensitive data, business applications, and cloud resources…
12 Aug Preparing For The Quantum Era: How Tech Companies Are Developing Next-Gen Cybersecurity Posted at 09:16h in Blogs by…
A widespread campaign featuring a malicious installer that saddles users with difficult-to-remove malicious Chrome and Edge browser extensions has been…
Aug 12, 2024Ravie LakshmananCybersecurity / Network Security The maintainers of the FreeBSD Project have released security updates to address a…
In the beginning of August 2024, Sonos released a security advisory in which they fixed two security vulnerabilities that were…
Head Mare, a hacktivist group targeting Russia and Belarus, leverages phishing campaigns distributing WinRAR archives to exploit CVE-2023-38831 for initial…
In the digital age, the dark web has emerged as a clandestine marketplace for illicit activities, including the sale of stolen data, illegal software and various forms of malware. The proliferation of…
Discover how researchers exploited vulnerabilities in Google’s Quick Share to achieve remote code execution (RCE). Learn about the “QuickShell” attack…