In 2023, no fewer than 94 percent of businesses were impacted by phishing attacks, a 40 percent increase compared to…
The threat landscape is significantly evolving, and cybersecurity researchers are continuously developing new security mechanisms to mitigate such evolving and…
After a good year of sustained exuberance, the hangover is finally here. It’s a gentle one (for now), as the…
Australian mining company Evolution Mining Limited has become the latest victim of a ransomware attack. The company, known for its…
Security researchers have uncovered severe vulnerabilities in the Ewon Cosy+, a widely used industrial remote access gateway tool, allowing them…
Aug 12, 2024Ravie LakshmananCritical Infrastructure / Vulnerability Cybersecurity researchers have identified a number of security shortcomings in photovoltaic system management…
A newly discovered OpenSSH vulnerability in FreeBSD systems has been reported. This critical flaw, identified as CVE-2024-7589, could allow attackers…
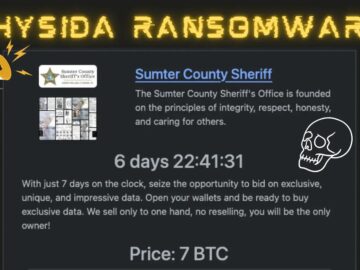
The Sumter County Sheriff’s Office has been victim to a ransomware attack orchestrated by the criminal group Rhysida. The cyberattack…
The UK’s National Cyber Security Centre (NCSC) recently hosted an unprecedented conference at its London headquarters, bringing together international government…
A new MS Office zero-day vulnerability (CVE-2024-38200) can be exploited by attackers to grab users’ NTLM hashes, Microsoft has shared…
Gartner highlights Cyble as a sample vendor in the Gartner® Hype Cycle™ for Managed IT Services, 2024, according to a…
Cybersecurity researchers have discovered an extensive hacker toolkit, revealing a comprehensive set of tools designed for various stages of cyberattacks….