EastWind campaign targets Russian organizations with sophisticated backdoors Pierluigi Paganini August 12, 2024 A campaign tracked as EastWind is targeting…
Researchers from Aqua identified critical vulnerabilities in six Amazon Web Services (AWS): CloudFormation, Glue, EMR, SageMaker, ServiceCatalog, and CodeStar. These…
Last week on Malwarebytes Labs: Last week on ThreatDown: Stay safe! Our business solutions remove all remnants of ransomware and…
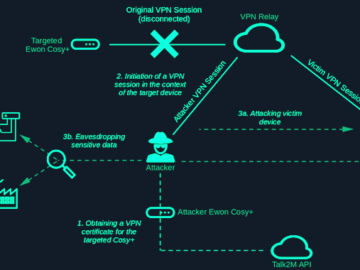
Aug 12, 2024Ravie LakshmananOperational Technology / Network Security Security vulnerabilities have been disclosed in the industrial remote access solution Ewon…
Google researchers have identified critical security vulnerabilities within Qualcomm’s Adreno GPU, potentially affecting billions of Android devices globally. If exploited,…
Software asset management (SAM) has evolved from simple back-office record-keeping to more complex licence and contract management that integrates innovative…
AMD is currently confronting a major security challenge involving the Sinkclose vulnerability, a critical flaw affecting a wide range of…
Microsoft found OpenVPN bugs that can be chained to achieve RCE and LPE Pierluigi Paganini August 12, 2024 Microsoft found…
U.S. authorities have arrested two believed administrators of the notorious WWH-Club, an online marketplace for stolen credit card information. The…
Scammers on the social media platform X (formerly known as Twitter) have escalated their tactics by exploiting global crises to…
As cloud computing continues to evolve, so do the challenges associated with securing digital environments. One of the most significant…
A critical security vulnerability has been discovered in OpenSSH implementations on FreeBSD systems, potentially allowing attackers to execute remote code…