Cisco has announced the integration of its Talos threat intelligence across multiple Splunk security products, marking a significant milestone in…
Jenkins, an open source automation server, has been found to have two security issues, one of which is a critical…
Sonos smart speakers flaw allowed to eavesdrop on users Pierluigi Paganini August 10, 2024 NCC Group discovered vulnerabilities in Sonos…
At the recent Black Hat USA conference, security researcher Michael Bargury unveiled alarming vulnerabilities within Microsoft Copilot, demonstrating how hackers…
A new APT group, dubbed Actor240524, launched a spear-phishing campaign targeting Azerbaijani and Israeli diplomats on July 1, 2024, where…
ADT Inc., a prominent security and automation solutions provider, reported that unauthorized actors accessed specific databases containing customer order information….
Mobile Device Management (MDM) is a device management solution for laptops, tablets, and smartphones used by organizations to enable them…
If the number of recent organisational closures is anything to go by, diversity, equity and inclusion (DEI) in the UK…
Attackers obtain system configuration files by taking advantage of software or protocols that are installed on devices, such as by…
Demand for graphics processing units or GPUs has exploded in recent years as video rendering and artificial intelligence systems have…
Kimsuky, a North Korean APT group, employs targeted phishing campaigns, leveraging DMARC exploitation to conceal social engineering, infiltrate university networks,…
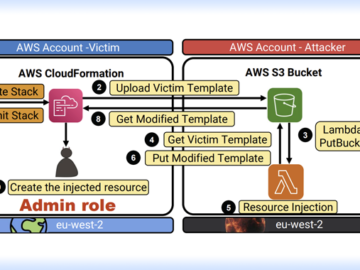
Aug 09, 2024Ravie LakshmananCloud Security / Data Protection Cybersecurity researchers have discovered multiple critical flaws in Amazon Web Services (AWS)…