In recent months, cybersecurity analysts have observed a troubling increase in the activity of Golddigger and Gigabud Android banking trojan. Since…
Microsoft’s latest intelligence report has revealed alarming efforts by Iranian state-linked groups to meddle in the 2024 US presidential election….
Russian cyber spies stole data and emails from UK government systems Pierluigi Paganini August 09, 2024 Earlier this year, Russian…
Researchers at Symantec have identified a new Linux ransomware variant linked to a bilingual (English and Spanish) double-extortion ransomware group….
Authorities have dismantled a “laptop farm” in Nashville, Tennessee, allegedly used to support the Democratic People’s Republic of Korea’s (DPRK)…
As cloud computing continues to evolve and integrate deeply into business operations, the need for robust cloud security tools becomes…
Aug 09, 2024Ravie LakshmananVulnerability / Network Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has disclosed that threat actors…
American building security giant ADT has confirmed that it experienced a cybersecurity incident after threat actors leaked allegedly stolen customer…
A critical vulnerability, identified as CVE-2024-7553, has been discovered in MongoDB. It could potentially allow attackers to take complete control…
The expectation of cyberattacks targeting the Olympic Games was widespread. Earlier this year, Mandiant released a report identifying likely attackers…
76% of security leaders recognize the pressing need to move to shorter certificate lifespans to improve security, according to Venafi….
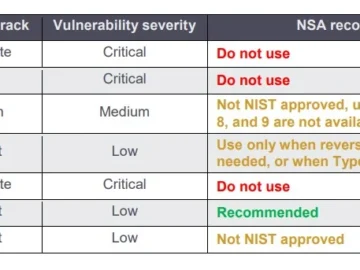
In a recent advisory, the Cybersecurity and Infrastructure Security Agency (CISA) has highlighted growing concerns regarding the exploitation of vulnerabilities…