The dark web refers to websites that are not on the regular internet but are instead hidden in a private…
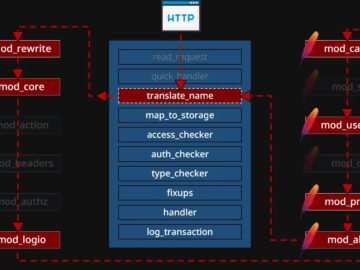
A recent research presentation at Black Hat USA 2024 revealed architectural vulnerabilities within the Apache HTTP Server, a widely used…
The Network and Information Security (NIS) 2 Directive is possibly one of the most significant pieces of cybersecurity regulation to…
The sophistication of cyber threats has escalated dramatically, with malicious actors’ deploying advanced tactics, techniques, and procedures (TTPs) to exploit…
Over half of key stakeholders including audit committees, company boards, and chief financial officers are looking to internal audit teams…
PoC exploit released for critical 0-click remote code execution (RCE) vulnerability affecting Windows Server. This flaw impacts Windows Server versions…
Here’s a look at the most interesting products from the past week, featuring releases from: Rapid7, AppOmni, Contrast Security, Elastic,…
The dark web refers to websites that are not on the regular internet but are instead hidden in a private…
When a bad software update from the security firm CrowdStrike inadvertently caused digital chaos around the world last month, the…
In a surprising move, the U.S. Securities and Exchange Commission (SEC) has decided not to bring charges against Progress Software…
Social media platform X agreed on Thursday not to train its AI systems for now using the personal data collected…
Microsoft reminded today that Exchange 2016 will reach the end of extended support next year on October 14 and shared…