Cryptocurrency scams have changed along with digital currencies and they now employ technological advancements like AI and deepfakes in their…
Monitoring evolving DDoS trends is essential for anticipating threats and adapting defensive strategies. The comprehensive Gcore Radar Report for the…
New York Attorney General Letitia James, in partnership with her counterparts in Connecticut and New Jersey, emphasized the gravity of…
A sophisticated phishing campaign has emerged, impersonating the Google Safety Centre to deceive users. This campaign is tricking unsuspecting individuals…
Zoom Video Communications has recently disclosed several critical vulnerabilities affecting its Workplace Apps, SDKs, and Rooms Clients. These vulnerabilities, identified…
In an age where digital privacy concerns are at an all-time high, the potential for hackers to track users through…
Aug 14, 2024Ravie LakshmananWindows Security / Vulnerability Microsoft on Tuesday shipped fixes to address a total of 90 security flaws,…
Microsoft has released its August 2024 Patch Tuesday update, addressing multiple vulnerabilities across its software ecosystem. This month’s update features…
In recent months, Britain has seen a concerning increase in smartphone thefts. Whether on the tube, during transit, or simply…
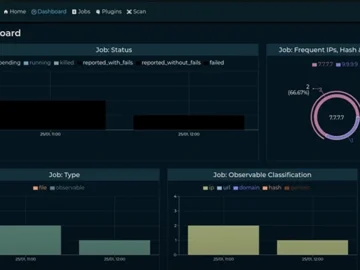
IntelOwl is an open-source solution designed for large-scale threat intelligence management. It integrates numerous online analyzers and advanced malware analysis…
In a potentially groundbreaking dispute, Delta Air Lines is threatening to sue CrowdStrike, a leading cybersecurity firm, for alleged negligence…
Cloud Security Specialist EPAM Systems | Chile | Remote – View job details As a Cloud Security Specialist, you will…