Airports were left crippled, healthcare systems were disrupted, supermarket check-outs malfunctioned, and journalists scrambled without the basic tools of the…
Threat actors attempted to capitalize CrowdStrike incident Pierluigi Paganini July 20, 2024 CrowdStrike warns that threat actors are exploiting the…
Microsoft says a faulty CrowdStrike Falcon update, which caused widespread outages by crashing Windows systems worldwide, also resulted in Windows…
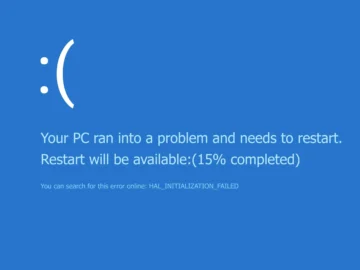
On July 19, 2024, CrowdStrike identified an issue in a content update for the Falcon sensor affecting Windows operating systems….
In the contemporary technological landscape, the allure of advanced artificial intelligence (AI) systems often captivates the collective imagination of the…
The week was particularly chock-full of dramatic security news. On Friday, a flawed update to CrowdStrike’s Falcon platform caused massive…
A routine software update by CrowdStrike on July 19, 2024, unintentionally stirred a major disruption across various infrastructures and organizations….
Cybersecurity experts have uncovered a concerning development following the recent CrowdStrike Falcon sensor issue that affected Windows systems on July…
Jul 20, 2024NewsroomCybercrime / Data Breach Law enforcement officials in the U.K. have arrested a 17-year-old boy from Walsall who…
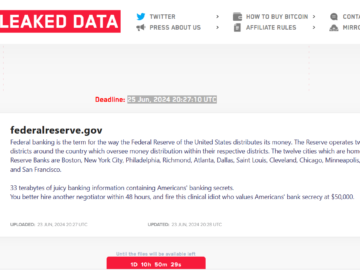
Russian nationals plead guilty to participating in the LockBit ransomware group Pierluigi Paganini July 20, 2024 Two Russian nationals pleaded…
Two foreign nationals from the notorious international ransomware group LockBit pleaded guilty in the in Newark federal court for participating…
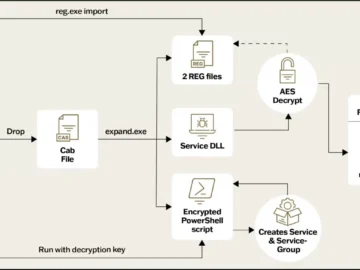
A China-linked hacking group known as Ghost Emperor has resurfaced with an updated version of its sophisticated Demodex rootkit, according…