Thank you for joining! Access your Pro+ Content below. 23 July 2024 Serving up a GenAI experience at Wimbledon Share…
Wiz, the Israeli cybersecurity firm, has made a strategic decision to reject a staggering $23 billion acquisition offer from Google’s…
Uninterrupted flow of power is essential for delivering critical services across the public sector, such as healthcare, emergency responses, and…
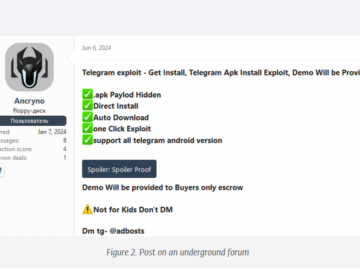
EvilVideo, a Telegram Android zero-day allowed sending malicious APKs disguised as videos Pierluigi Paganini July 22, 2024 EvilVideo is a…
The Land Registry agency in Greece has announced that it suffered a limited-scope data breach following a wave of 400…
As the world prepares for the start of the Paris Olympics later this week, athletes and spectators alike are filled…
HOYTS has deployed Cisco hardware and Optus services across its Australian and New Zealand operations as part of a digital…
Microsoft releases a recovery tool to fix CrowdStrike outages that crippled IT systems worldwide. The tool offers two repair options:…
iTnews is proud to announce the launch of a new iteration of its technology leadership ‘Benchmark Awards’ program, this time…
Delta Air Lines continued to struggle to restore its operations on Monday, three days after a global IT outage snarled…
CrowdStrike is actively working to resolve a defect in a content update that struck about 8.5 million Windows machines on…
A 24-year-old Katy, Texas resident, has been sentenced to nine months in federal prison for running a website that facilitated…