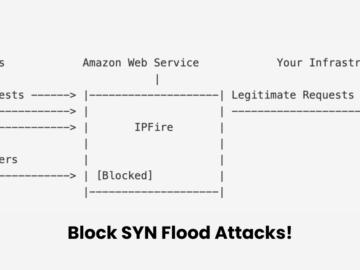
IPFire, a well-known open-source firewall solution, has introduced a new feature to protect systems from SYN Flood attacks, enhancing cybersecurity…
Threat actors often attack dating apps to steal personal data, including sensitive data and location details, which can be used…
Identity governance and administration (IGA) is a critical part of modern business. It’s one of the single most important pieces…
Meta has been given time till September 1, 2024, to respond to concerns raised by the European Commission over its…
In this podcast, we look at sustainable storage with Grant Caley, UK and Ireland solutions director at NetApp. Caley talks…
Google is planning to keep third-party cookies in its Chrome browser, after years of pledging to phase out the tiny…
Recently, it has been observed that several campaigns are using Cloudflare’s WARP service to target susceptible internet-facing services. The primary…
When it comes to the cyber threat landscape, change is the only constant: the inevitable interplay between cybercriminals and law…
Jul 23, 2024NewsroomICS Malware / Critical Infrastructure Cybersecurity researchers have discovered what they say is the ninth Industrial Control Systems…
UK innovation agency Digital Catapult has set it sights on helping the creative industry grow by revamping its production processes…
A Suffolk County ransomware attack has left a lasting impact on the community, with the county approving over $25 million…
Australia’s eSafety commissioner has made a pitch for extra “technical regulation powers” that it could use against certain online app…