In this Help Net Security interview, Anand Pashupathy, VP & GM, Security Software & Services Division at Intel, explains how…
Jul 23, 2024NewsroomThreat Detection / Website Security Threat actors have been observed using swap files in compromised websites to conceal…
A new dark web threat has emerged on the market, leveraging football sponsorship controversies to deploy “Vigorish Viper,” a sophisticated…
Affiliate marketing is a practice where firms compensate associates for bringing visitors or customers to their websites. It comprises sellers,…
The United States has designated Yuliya Vladimirovna Pankratova and Denis Olegovich Degtyarenko, two members of the Russian hacktivist group Cyber…
The fintech market is experiencing a swift transformation driven by emerging technologies like Open Finance and GenAI, as highlighted by…
Jul 23, 2024The Hacker NewsCorporate Security / Data Protection The initial onboarding stage is a crucial step for both employees…
In today’s digital age, the dark web has emerged as a notorious underworld of the internet, accessible only through specialized…
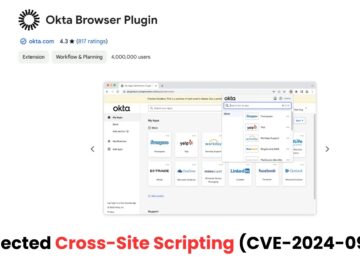
Okta Browser Plugin is available on multiple browsers like Edge, Chrome, Safari, and Firefox. Combining all these browsers, the plugin…
The National Crime Agency (NCA) has successfully infiltrated and dismantled one of the most notorious Distributed Denial of Service (DDoS)…
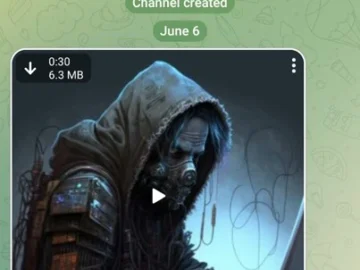
ESET researchers discovered a zero-day exploit, which targets the Telegram app for Android, that appeared for sale for an unspecified…
The cloud has become an essential component of modern technology, storing everything from photos to important files. While it offers…