Booktopia has entered voluntary administration after struggling with the expense of transitioning to a $12 million robot-enabled warehouse facility and to…
A Pakistan-linked hacking group has unleashed an updated version of its Android spyware, expanding its reach to target mobile gamers,…
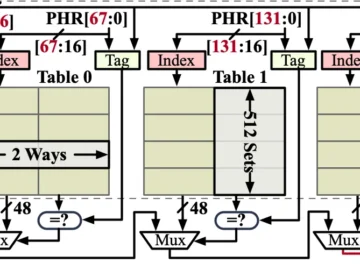
Security researchers have identified a novel side-channel attack that can compromise the security of modern Intel CPUs variants, including Raptor…
Iress has completed an investigation into a breach of its OneVue platform, finding it was isolated to a “limited” part…
The European Commission has found that Meta’s “pay or consent” advertising model breaches the Digital Markets Act (DMA). The preliminary…
National Archives of Australia is set to perform a “health check” on 15 service desks atop ServiceNow, its first such…
The Biden administration has revoked eight licenses this year that had allowed some companies to ship goods to Chinese telecoms…
Australia is giving the internet industry six months to come up with an enforceable code detailing how it will stop…
The Xbox gaming service is currently down due to a major outage, impacting customers worldwide and preventing them from signing into their…
Evolve Bank data breach impacted fintech firms Wise and Affirm Pierluigi Paganini July 02, 2024 Fintech firms Wise and Affirm…
Patelco Credit Union has disclosed it experienced a ransomware attack that led to the proactive shutdown of several of its…
French authorities seized servers and proceeds worth millions belonging to the “Coco” chat website, a free-for-all online platform that facilitated…