The U.S. Department of Justice has asked an appeals court to reject legal challenges to a law requiring ByteDance, TikTok’s…
The ACCC has made a case for the ‘broadband tax’ on NBN-equivalent services to be expanded to 4G and 5G…
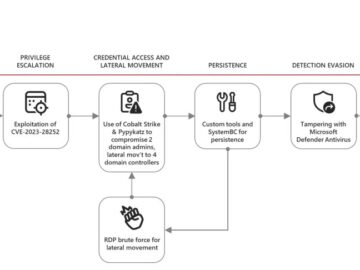
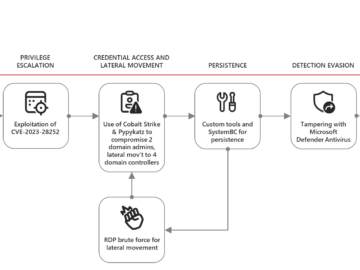
The threat actor group UNC4393, known for deploying BASTA ransomware, has undergone continuous changes in its tactics since mid-2022. Researchers…
Microsoft researchers have observed multiple ransomware operators exploiting a recently patched vulnerability in ESXi hypervisors to gain full administrative control…
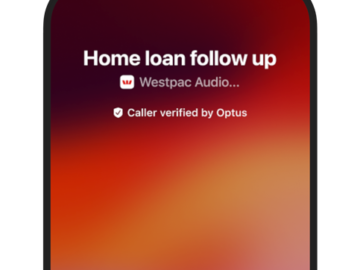
Westpac will introduce in-app calling inside of its mobile banking app within months as a security measure, with the service…
A new version of the Android spyware ‘Mandrake’ has been found in five applications downloaded 32,000 times from Google Play,…
Microsoft investors will have one big question when the tech giant reports earnings: has growth in its Azure cloud-computing business…
Ransomware gangs exploit recently patched VMware ESXi bug CVE-2024-37085 Pierluigi Paganini July 29, 2024 Microsoft warns that ransomware gangs are…
Microsoft Outlook can be turned into a C2 beacon to remotely execute code, as demonstrated by a new red team…
The Malaysian Digital Ministry is increasing efforts to secure the country’s digital landscape as it attracts major investments from foreign…
Hewlett Packard Enterprise (HPE) is expected to secure unconditional EU antitrust approval for its US$14 billion ($21.4 billion) acquisition of…
Cyble Research & Intelligence Labs (CRIL) researchers have analyzed more than 100 security vulnerabilities in the last two weeks, with…