A recent global IT outage linked to CrowdStrike, a leading cybersecurity company, has resulted in an estimated $5.4 billion in…
In the DevSecOps Blueprint whitepaper, GitGuardian outlines a robust foundation for building an automated and technology-driven DevSecOps Program that addresses…
Despite a broad range of efforts to close the cybersecurity skills gap, one expert has warned that recruiters’ focus on…
NAB has emerged as an adopter of Microsoft’s Copilot for Security, using it within Intune as part of its oversight…
Euro zone banks have “room for improvement” in their cyber security, starting with how they would keep their business running…
Around 80 countries reached have agreement on rules governing global digital commerce including recognition of e-signatures and protection against online…
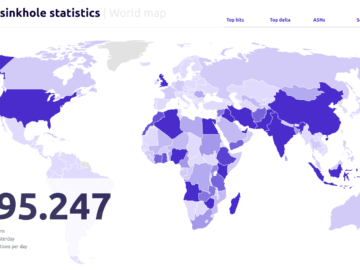
French authorities launch disinfection operation to eradicate PlugX malware from infected hosts Pierluigi Paganini July 28, 2024 French authorities and…
Security Affairs Malware Newsletter – Round 4 Pierluigi Paganini July 28, 2024 Security Affairs Malware newsletter includes a collection of…
Once upon a time, when we used to have to go to physical stores to get the products we needed,…
Major Cyber Threats Powered by AI Many have embraced artificial intelligence as a new paradigm, with some even going so…
The notorious ransomware group Cicada3301 has claimed responsibility for a significant data breach at Singapore-based Tri-Star Display Pte Ltd. According…
In an era where digital devices dominate our daily lives, it’s common for households to have multiple smart home devices….