San Francisco, CA – OpenAI has announced the launch of SearchGPT, a groundbreaking prototype designed to revolutionize how users search…
The U.S. Department of Justice (DoJ) on Thursday unsealed an indictment against a North Korean military intelligence operative for allegedly…
Former government minister Vince Cable said the Post Office lied to the government to prevent the truth about the mistreatment…
Healthcare organizations are increasingly becoming prime targets for cyberattacks. The combination of limited budgets, a shortage of dedicated cybersecurity staff,…
The PKfail vulnerability is a significant security issue affecting over 200 device models of Secure Boot. PKfail is a critical…
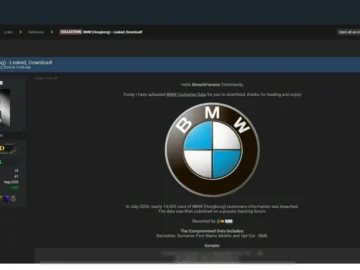
In a significant blow to data privacy, BMW has reported a major data breach affecting approximately 14,000 customers in Hong…
Terrorist Activity is Accelerating in Cyberspace – Risk Precursor to Summer Olympics and Elections Pierluigi Paganini July 26, 2024 Terrorist…
A vulnerability in OpenStack’s Nova component has been identified, potentially allowing hackers to gain unauthorized access to cloud servers. This…
Play Ransomware and LockBit Ransomware have reportedly allied to enhance their capabilities in launching cyber attacks. This collaboration, which involves…
On June 3rd of this year, Synnovis, a provider of technology and pathology services, fell victim to a ransomware attack,…
Progress Software has fixed a critical vulnerability (CVE-2024-6327) in its Telerik Report Server solution and is urging users to upgrade…
Jul 26, 2024Mohit KumarEnterprise Security / Network Security CrowdStrike is alerting about an unfamiliar threat actor attempting to capitalize on…