The Australian government’s Essential Eight provides a useful framework and basis for achieving a baseline of cyber security and mitigating…
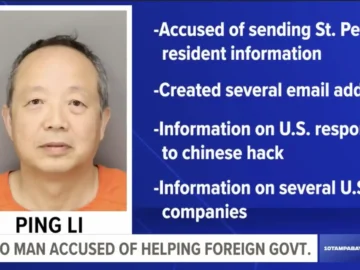
A recent federal indictment accuses Ping Li, a 59-year-old resident of Wesley Chapel, Florida, of conspiring to act as an…
The NSW government has been asked to appoint ‘chief AI officers’, both at a whole-of-government and department and agency level,…
North Korean hackers have conducted a global cyber espionage campaign in efforts to steal classified military secrets to support Pyongyang’s…
OpenAI is throwing its hat into the AI search ring with SearchGPT, a prototype designed to revolutionize how users find…
In response to an increase in cyberattacks, Hong Kong is taking its first steps to introduce comprehensive cybersecurity legislation. The…
Global insured losses from last week’s massive IT outage are likely to range from US$400 million to US$1.5 billion ($612…
Hundreds of UEFI products from 10 vendors are susceptible to compromise due to a critical firmware supply-chain issue known as…
Nine Entertainment is continuing to refine a single view of customer capability it has built on a Google Cloud foundation,…
Progress Software fixed critical RCE CVE-2024-6327 in the Telerik Report Server Pierluigi Paganini July 25, 2024 Progress Software addressed a…
Threat actors are chaining together ServiceNow flaws using publicly available exploits to breach government agencies and private firms in data…
Inside Amazon.com’s chip lab in Austin, Texas, half a dozen engineers on a Friday afternoon put a closely guarded new…