Cybersecurity experts have uncovered a sophisticated variant of the LummaC2 malware that leverages the popular Steam gaming platform as a…
In response to a notable increase in cyberattacks on Guernsey, the Office of the Data Protection Authority (ODPA) has issued…
July 25, 2024: The Cyber Express (TCE) is excited to announce its media partnership with the highly anticipated Black Hat…
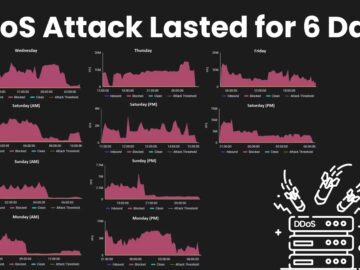
A financial institution in the Middle East endured a record-breaking Distributed Denial of Service (DDoS) attack for six days. The…
Jul 25, 2024NewsroomDNS Security /Vulnerability The Internet Systems Consortium (ISC) has released patches to address multiple security vulnerabilities in the…
A critical security vulnerability has been discovered in the Progress® Telerik® Report Server, potentially allowing attackers to execute remote code…
BIND (Berkeley Internet Name Domain) is an open-source DNS software system with an authoritative server, a recursive resolver, and related…
A zero-day security flaw in Telegram’s mobile app for Android called EvilVideo made it possible for attackers to malicious files…
GitLab has released new Community Edition (CE) and Enterprise Edition (EE) versions to address multiple vulnerabilities. Among these, a high-severity…
Several prominent Russian bank clients experienced issues with their mobile apps and websites. According to Downdetector, complaints began to surge…
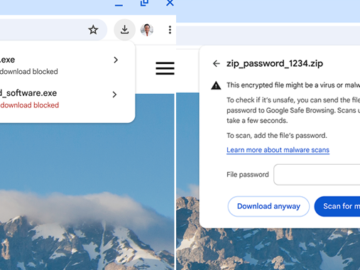
Jul 25, 2024NewsroomBrowser Security / Data Protection Google said it’s adding new security warnings when downloading potentially suspicious and malicious…
Mimecast, a global Human Risk Management (HRM) platform, has announced its acquisition of Code42, a prominent name in insider threat…