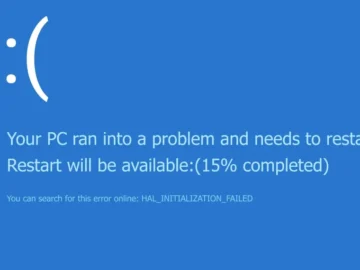
The massive CrowdStrike outage will cost Fortune 500 companies more than $5 billion – and 90% of that won’t be…
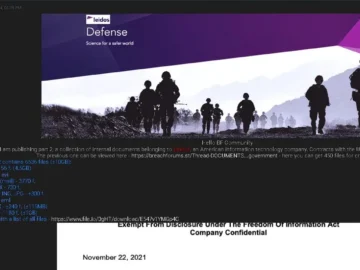
Hackers have leaked internal documents stolen from Leidos Holdings Inc., a major U.S. government IT services provider, according to a…
U.S. CISA adds Microsoft Internet Explorer and Twilio Authy bugs to its Known Exploited Vulnerabilities catalog Pierluigi Paganini July 24,…
Threat actors known as ‘Stargazer Goblin’ have created a malware Distribution-as-a-Service (DaaS) from over 3,000 fake accounts on GitHub that push…
The Defence Digital Group’s move to rebuild its workforce from 20 percent government employees to 60 percent will result in…
(Reuters) -Hackers have leaked internal documents stolen from Leidos Holdings, one of the largest IT services providers to governments, Bloomberg…
U.S. CISA adds Microsoft Internet Explorer and Twilio Authy bugs to its Known Exploited Vulnerabilities catalog Pierluigi Paganini July 24,…
Apple is likely to introduce its foldable iPhone as early as 2026, the Information reported, that could mark the biggest…
The U.S. security agencies are warning technology startups to be wary of foreign venture capital investments that may be attempts…
Docker has issued security updates to address a critical vulnerability impacting certain versions of Docker Engine that could allow an…
Under-fire cyber firm CrowdStrike has published an initial post incident review setting out more information on the update-gone-wrong that brought…
Microsoft has fixed a known Windows 10 update issue that broke Microsoft Connected Cache (MCC) node discovery on enterprise networks….