Responsibly Adopting Technology to Improve Law Firm Productivity Lawyers face incredible pressure in their jobs to perform accurately and quickly….
A bug in the Content Validator – a software element CrowdStrike relies on for testing and validating Rapid Response Content…
Security questionnaires aren’t just an inconvenience — they’re a recurring problem for security and sales teams. They bleed time from…
Since it was founded in 1754, The Royal and Ancient Golf Club (The R&A) has been a bastion of sporting…
Indian cryptocurrency exchange WazirX has issued an update in response to a recent cyberattack that saw hackers steal over $230…
The entire database for the notorious BreachForums v1 hacking forum was released on Telegram Tuesday night, exposing a treasure trove…
The popular LiteSpeed Cache plugin for WordPress has been found vulnerable to a Cross-Site Request Forgery (CSRF) attack, which could…
This is, incidentally, how he plans to fund the operation—the basic version of WebXray will be available to all, but…
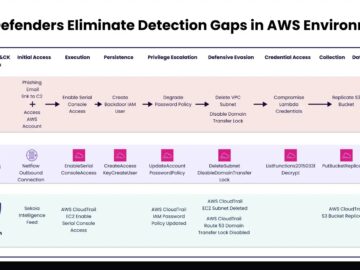
As enterprises increasingly migrate their workloads to cloud infrastructure, the need for robust security measures becomes more pressing. Unlike traditional…
New Stealer Campaign Exploits Windows SmartScreen Vulnerability (CVE-2024-21412) – This large-scale attack targets Windows users, stealing passwords, browsing history, and…
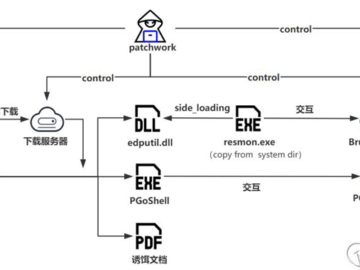
Jul 24, 2024NewsroomCyber Espionage / Threat Intelligence The threat actor known as Patchwork has been linked to a cyber attack…
The India Union Budget 2024, released yesterday by Indian Finance Minister Nirmala Sitharaman, marks the first budget under the BJP-led…