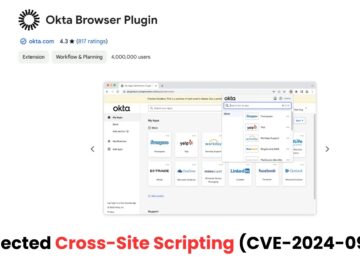
Okta Browser Plugin is available on multiple browsers like Edge, Chrome, Safari, and Firefox. Combining all these browsers, the plugin…
The National Crime Agency (NCA) has successfully infiltrated and dismantled one of the most notorious Distributed Denial of Service (DDoS)…
ESET researchers discovered a zero-day exploit, which targets the Telegram app for Android, that appeared for sale for an unspecified…
The cloud has become an essential component of modern technology, storing everything from photos to important files. While it offers…
Ransomware attacks are back in the news with vengeance, striking several high profile victims. There are almost too many attacks…
US Gov sanctioned key members of the Cyber Army of Russia Reborn hacktivists group Pierluigi Paganini July 23, 2024 The…
Google has scrapped its plan to kill third-party cookies in Chrome and will instead introduce a new browser experience that…
Wiz, the $12 billion cloud security startup, has rejected a $23 billion acquisition offer from Google parent Alphabet. Fortune viewed…
Lvivteploenergo didn’t respond to WIRED’s request for comment, nor did the SBU. Ukraine’s cybersecurity agency, the State Services for Special…
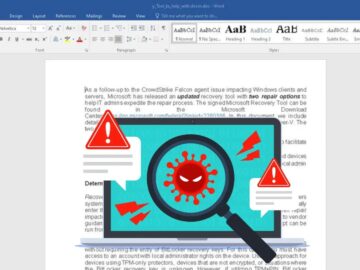
Threat actors have been found exploiting a recently discovered bug in CrowdStrike’s software that causes a Blue Screen of Death…
Normal0 falsefalsefalse EN-US /* Style Definitions */table.MsoNormalTable{mso-style-name:”Table Normal”;mso-tstyle-rowband-size:0;mso-tstyle-colband-size:0;mso-style-noshow:yes;mso-style-priority:99;mso-style-parent:””;mso-padding-alt:0in 5.4pt 0in 5.4pt;mso-para-margin:0in;mso-pagination:widow-orphan;mso-hyphenate:none;font-size:10.0pt;mso-bidi-font-size:11.0pt;font-family:”Calibri”,sans-serif;mso-ascii-font-family:Calibri;mso-ascii-theme-font:minor-latin;mso-hansi-font-family:Calibri;mso-hansi-theme-font:minor-latin;mso-bidi-font-family:Calibri;mso-bidi-theme-font:minor-bidi;mso-font-kerning:1.0pt;mso-ligatures:standardcontextual;} The 2024 Paris Olympic Games, set to begin later…
As organizations increasingly adopt third-party AI tools to streamline operations and gain a competitive edge, they also invite a host…