In Saudi Arabia, where economic diversification and institutional reform are reshaping the role of business, technology is becoming a central…
Cisco has released security updates to patch a critical vulnerability in the Unified Contact Center Express (UCCX) software, which could…
A critical remote code execution (RCE) flaw in three official extensions for Anthropic’s Claude Desktop. These vulnerabilities, affecting the Chrome,…
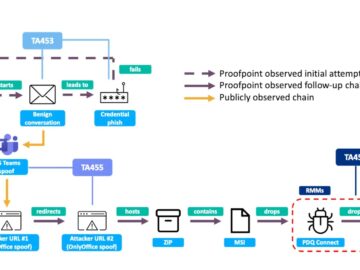
Proofpoint Threat Research has identified a previously unknown Iranian threat actor, dubbed UNK_SmudgedSerpent, that conducted sophisticated phishing campaigns against academics…
Cybersecurity researchers at Doctor Web have discovered a targeted attack against a Russian government-owned organisation carried out by a hacker…
Taylor Fox, Instagram and social media contributor at Cybercrime Magazine, has been hacking away at the top cybersecurity stories since…
Incident responders from Mandiant have wrapped up their investigation into the SonicWall cloud backup service hack, and the verdict is…
On November 3, 2025, blockchain security monitoring systems detected a sophisticated exploit targeting Balancer V2’s ComposableStablePool contracts. An attacker executed…
Security researchers have uncovered a sophisticated attack campaign attributed to Kimsuky, the North Korean-backed threat group known for conducting espionage…
Introduction Financial institutions are facing a new reality: cyber-resilience has passed from being a best practice, to an operational necessity,…
Django, one of the most popular Python web development frameworks, has disclosed two critical security vulnerabilities that could allow attackers…
Cisco has issued a critical security advisory addressing two severe vulnerabilities in its Unified Contact Center Express (CCX) platform that…