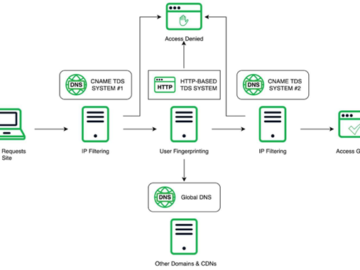
The relationship between various TDSs and DNS associated with Vigorish Viper and the final landing experience for the user A…
Amazon employees are calling the contents of the company’s annual environmental report into question, including the retail giant’s claim to…
Cisco recently disclosed that its RV340 and RV345 Dual WAN Gigabit VPN Routers have a significant flaw in the upload…
SonicWall has disclosed a critical heap-based buffer overflow vulnerability in its SonicOS IPSec VPN. This flaw, identified as CVE-2024-40764, can…
The Superior Court of Los Angeles County, the United States’ largest trial court, has suffered a crippling ransomware attack. This…
22 Jul Boris Karloff Is A Cybersecurity Expert’s Best Friend Posted at 09:03h in Blogs by Di Freeze This week…
By now, most people are aware of – or have been personally affected by – the largest IT outage the…
Jul 22, 2024NewsroomCloud Security / Phishing Attack A Latin America (LATAM)-based financially motivated actor codenamed FLUXROOT has been observed leveraging…
Opportunist cyber criminals are the most pressing immediate threat arising from the 19 July Microsoft outage, which caused millions of…
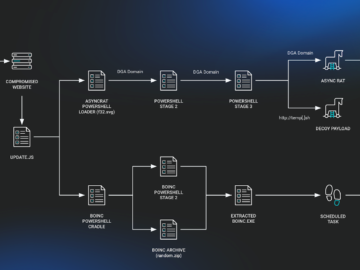
SocGholish malware used to spread AsyncRAT malware Pierluigi Paganini July 22, 2024 The JavaScript downloader SocGholish (aka FakeUpdates) is being…
The Spanish authorities have arrested three individuals for using DDoSia, a distributed denial of service platform operated by pro-Russian hacktivists,…
The FBI successfully unlocked the Samsung smartphone of the deceased Trump shooter within 40 minutes, thanks to the digital forensics…