If you’re one of the millions of Americans who live within range of its 450 intercontinental ballistic missile silos, the…
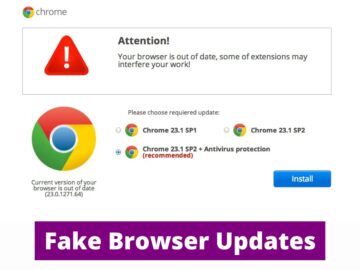
SocGholish malware, also known as FakeUpdates, has exhibited new behavior since July 4th, 2024, as the infection chain still begins…
Former coalition government ministers were “handled” by civil servants who “covered their own backs” while evidence of a scandal at…
The increasing prevalence of scams and data breaches makes safeguarding your personal information more challenging than ever. Cybercriminals are becoming…
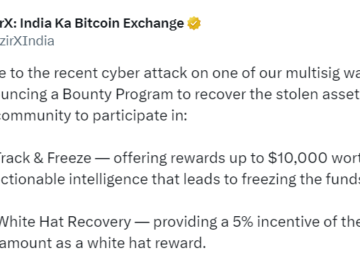
In response to the recent WazirX cyberattack that led to the theft of $230 million from one of its multisig…
Advanced persistent threat group APT41 launched an extended attack that successfully compromised a number of companies in the media and…
UK police have arrested a 17-year-old boy from Walsall in connection with a notorious cyber hacking group. This group has…
The UK government has sought to be proactive in its approach to addressing climate change, committing to ambitious targets such…
In the aftermath of the CrowdStrike and Microsoft outage that crippled critical infrastructure worldwide—impacting airports, hospitals, schools, and government offices—the…
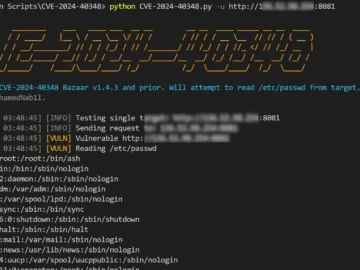
A critical security flaw, CVE-2024-40348, has emerged in Bazaar v1.4.3, posing substantial risks due to its potential for directory traversal…
UK police arrested a 17-year-old linked to the Scattered Spider gang Pierluigi Paganini July 22, 2024 Law enforcement arrested a…
Recordings heard by Calcalist reveal the shocking lengths to which litigants would go to influence a trial. The right-hand man…