15 Aug Cybercrime Magazine Heads To Fire Island For The Day Posted at 09:21h in Blogs by Di Freeze This…
A recent Digital Forensics and Incident Response (DFIR) report has uncovered various sophisticated tools threat actors employ to bypass major…
Google’s flagship Pixel smartphone line touts security as a centerpiece feature, offering guaranteed software updates for seven years and running…
With ransomware attacks reaching unprecedented levels, businesses face tough decisions when their data is held hostage. While the temptation to…
Today, ICT-related incidents remain rampant, with the scourge of data breaches showing no sign of abating. This year,millions of records will unfortunately once again be affected with the ramifications being severe and the average…
Aug 15, 2024Ravie LakshmananCyber Attack / Social Engineering Russian and Belarusian non-profit organizations, Russian independent media, and international non-governmental organizations…
The research identifies a critical security vulnerability in GitHub Actions artifacts, enabling unauthorized access to tokens and secrets within CI/CD…
Aug 15, 2024Ravie LakshmananRansomware / Cybercrime A cybercrime group with links to the RansomHub ransomware has been observed using a…
Public admission of failure takes courage. In trying to limit reputational damage to his cybersecurity company, CrowdStrike president Michael Sentonas…
In collaboration with Access Now and other civil society organizations, Citizen Lab exposed a sophisticated attack dubbed as “Rivers of…
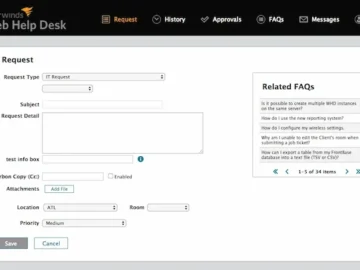
SolarWinds has fixed a critical vulnerability (CVE-2024-28986) in its Web Help Desk (WHD) solution that may allow attackers to run…
Aug 15, 2024The Hacker NewsIdentity Security / Threat Detection The Emergence of Identity Threat Detection and Response Identity Threat Detection…