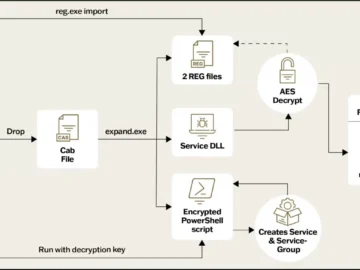
Two foreign nationals from the notorious international ransomware group LockBit pleaded guilty in the in Newark federal court for participating…
A China-linked hacking group known as Ghost Emperor has resurfaced with an updated version of its sophisticated Demodex rootkit, according…
CrowdStrike has provided its first technical explanation for a file update that bricked Windows machines worldwide. The vendor said in a…
The security firm CrowdStrike inadvertently caused mayhem around the world on Friday after deploying a faulty software update to the…
In a week that saw a cryptocurrency exchange lose $235 million to hackers and a botched migration that led to…
A 17-year-old from Walsall, England, has been apprehended in connection with the infamous Scattered Spider ransomware syndicate. The teen suspect…
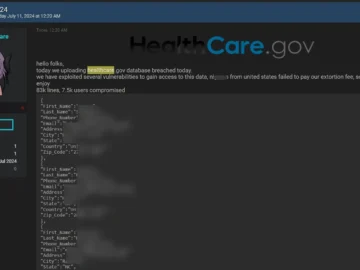
In today’s digital age, healthcare data has become a prime target for cybercriminals. With a single health record fetching up…
MediSecure data breach impacted 12.9 million individuals Pierluigi Paganini July 19, 2024 Personal and health information of 12.9 million individuals was…
A faulty update from the cybersecurity vendor CrowdStrike crashed countless Windows computers and sent them into a “Blue Screen of…
Nope, that headline’s not a typo. Over one thousand percent. The Identity Theft Resource Center (ITRC) tracked 1,041,312,601 data breach…
MediSecure, an Australian prescription delivery service provider, revealed that roughly 12.9 million people had their personal and health information stolen in…
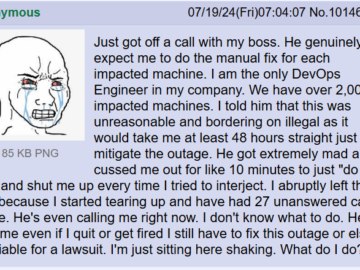
The world is 16+ hours into what looks like the biggest IT outage in history, triggered by a defective update…