The cyberattack on India’s biggest cryptocurrency exchange WazirX has sent shockwaves through the crypto community. The WazirX hack on July…
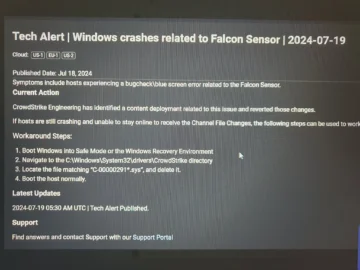
A massive number of Windows users worldwide have been grappling with a vexing issue: the Blue Screen of Death (BSOD)….
Cisco fixed a critical flaw in Security Email Gateway that could allow attackers to add root users Pierluigi Paganini July…
Google has announced the release of Chrome 126, a critical security update that addresses 10 vulnerabilities, including 8 high-severity flaws…
Chainalysis has launched Operation Spincaster, an initiative to disrupt approval phishing scams that have drained billions from victims’ wallets. This…
France Cybersecurity Agency, ANSSI, has issued a stark warning regarding the upcoming Paris Olympics 2024, cautioning that the event’s IT…
Amar Tagore, a third-year cybersecurity student, has been sentenced to 21 months in jail for his role in creating and…
A critical vulnerability identified as CVE-2024-21181 has been discovered in the Oracle WebLogic Server, posing a significant risk to affected…
Data Pseudonymization and Data Anonymization are crucial techniques in data protection and privacy. They offer several benefits that are essential…
A significant portion of the U.S. Securities and Exchange Commission’s (SEC) high-profile lawsuit against SolarWinds, the IT software company at…
Here’s a look at the most interesting products from the past week, featuring releases from AuditBoard, BlueVoyant, Druva, Invicti Security,…
Attackers consistently discover and exploit software vulnerabilities, highlighting the increasing importance of robust software security, according to OpenSSF and the…