Jul 19, 2024NewsroomCryptocurrency / Cybercrime Indian cryptocurrency exchange WazirX has confirmed that it was the target of a security breach…
As GenAI models used for natural language processing, image generation, and other complex tasks often rely on large datasets that…
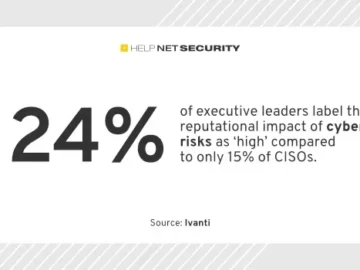
Cyber threats are advancing quickly in size and sophistication, largely because of the rapid evolution of technology, increasing sophistication of…
Researchers have observed a seemingly innocuous software installer named HotPage.exe being used to deploy a Microsoft-signed driver with the capability…
Pueblo County School District 70 is taking steps to address a recent data breach and ransomware attack that may have…
About 12.9 million Australians are impacted by the breach of defunct electronic prescription provider MediSecure, with 6.5TB of personal and…
Dark web monitoring is essential for CEOs in the banking industry to combat the escalating threat of cybercrime. In 2023,…
Google will infuse artificial intelligence into the US broadcast of the Paris Olympics, allowing sports commentators to use AI to…
A cybercriminal gang that researchers track as Revolver Rabbit has registered more than 500,000 domain names for infostealer campaigns that…
ANZ Banking Group is starting to see some uneven benefits distribution from its use of AI pair programming, with training…
A US judge dismissed most of a Securities and Exchange Commission lawsuit accusing software company SolarWinds of defrauding investors by…
Although not new, Registered Domain Generation Algorithms (RDGAs) have become a major cybersecurity threat, exploited by threat actors to bypass…