Threat actors often attack VMware ESXi servers since they accommodate many virtual machines, which link to a variety of systems…
FIN7, a notorious cybercrime gang, is back with a new bag of tricks! Learn about FIN7’s evolving tactics, including ransomware…
As the cyber workforce skills gap persists, companies that fail to upskill their IT teams with the knowledge to defend…
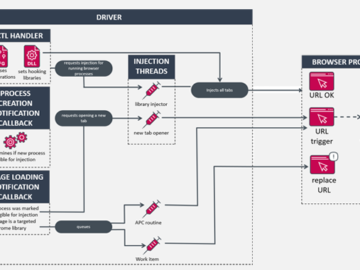
Jul 18, 2024NewsroomMalware / Windows Security Cybersecurity researchers have shed light on an adware module that purports to block ads…
Cisco has fixed a critical severity vulnerability that lets attackers add new users with root privileges and permanently crash Security…
Researchers examined how connection tracking, a fundamental function in operating systems, can be exploited to compromise VPN security and identified…
Since October 2023, MuddyWater, which is an Iranian threat group linked to MOIS, has escalated its phishing campaigns in Middle…
18 Jul The Importance Of Women In Cybersecurity Posted at 08:54h in Blogs by Di Freeze This week in cybersecurity…
CISSP carries clout. As the world’s leading cybersecurity certification, it opens many professional opportunities worldwide. Find out what led 14…
Breaking up is hard to do, but for younger Americans today, ending a romantic relationship requires more than a heart-to-heart…
Jul 18, 2024The Hacker NewsApp Security / Security Awareness Let’s face it: AppSec and developers often feel like they’re on…
IBM has received a significant contract from the U.S. Agency for International Development (USAID) to enhance cybersecurity response efforts in…