The Kamala Harris presidential campaign has recently been thrust into the spotlight following reports of foreign influence in the 2024…
Adobe has released patches for 72 security vulnerabilities across its popular software products. This effort, spearheaded by Adobe’s Product Security…
NetSPI discovered that Microsoft Outlook is vulnerable to authenticated remote code execution (CVE-2024-21378) due to improper validation of synchronized form…
Columbus Mayor Andrew Ginther addressed the public on the recent City of Columbus cyberattack that targeted the city’s IT infrastructure…
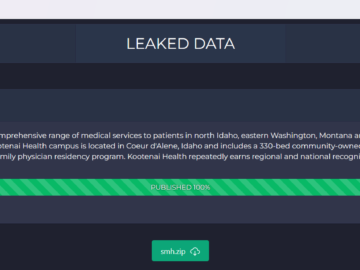
Kootenai Health data breach impacted 464,000 patients Pierluigi Paganini August 14, 2024 cc suffered a data breach impacting over 464,000…
SAP has released its August 2024 security patch update, addressing 17 new vulnerabilities, including two critical flaws that could allow…
Two men living a life of luxury in Florida have been charged with cyber fraud after authorities became suspicious of…
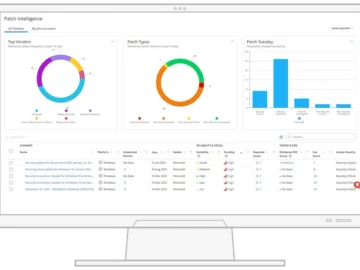
Ivanti announced new features for Ivanti Neurons for Patch Management to help expand patch settings configuration to allow for multiple…
Aug 14, 2024Ravie LakshmananThreat Intelligence / Cyber Attack The China-backed threat actor known as Earth Baku has diversified its targeting…
Tenable Research has uncovered significant security vulnerabilities in Microsoft’s Azure Health Bot Service, a cloud platform designed to enable healthcare…
Researchers studied the infrastructure behind clickbait PDF attacks by analyzing a large dataset of real-world PDFs to identify clickbait ones…
Aug 14, 2024Ravie LakshmananVulnerability / Network Security Ivanti has rolled out security updates for a critical flaw in Virtual Traffic…