A dangerous two-stage malware threat, LeakyInjector and LeakyStealer, that targets cryptocurrency wallets and personal browser information explicitly. The malware duo…
Cybersecurity researchers have uncovered a sophisticated phishing campaign that exploits compromised hotel booking accounts to defraud travellers worldwide. The campaign,…
IT leaders need to weigh up the drive to adopt new, exciting innovation with the technical debt and mission-critical legacy…
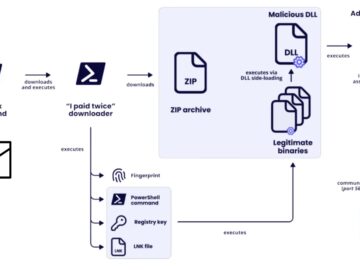
In July 2025, a sophisticated hacker group known as Cavalry Werewolf executed a targeted campaign against Russian government institutions, compromising…
Datadog Security Research has uncovered a sophisticated supply chain attack targeting the npm ecosystem, involving 17 malicious packages across 23…
Nov 07, 2025Ravie LakshmananData Protection / Malware Google on Thursday said it’s rolling out a dedicated form to allow businesses…
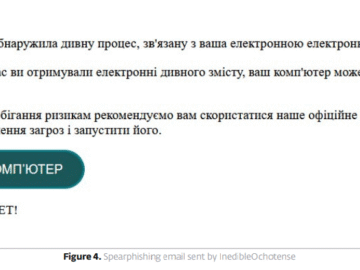
Russia-linked APT InedibleOchotense impersonates ESET to deploy backdoor on Ukrainian systems Pierluigi Paganini November 07, 2025 Russia-linked group InedibleOchotense used…
Amazon has disclosed a significant security vulnerability in its WorkSpaces client for Linux that could allow unauthorized users to extract…
Security researchers have developed a new technique that leverages call gadgets to insert arbitrary modules into the call stack during…
OPNsense has released an update focused on eliminating security vulnerabilities and improving firewall performance. The latest version includes third-party security…
The OPNsense project has released version 25.7.7, delivering critical security improvements and performance enhancements to strengthen enterprise firewall deployments. This…
Businesses are increasingly being pulled into lawsuits over how they collect and share user data online. What was once the…