The Volcano Demon group has been discovered spreading a new ransomware called LukaLocker, which targets Idealease Inc., a truck leasing…
On May 31, 2024, as a result of the hacking 4502.9 BTC (worth approximately $308M) were stolen from the Japanese…
The Information Commissioner’s Office (ICO) has strongly reprimanded the London Borough of Hackney over a series of failings that led…
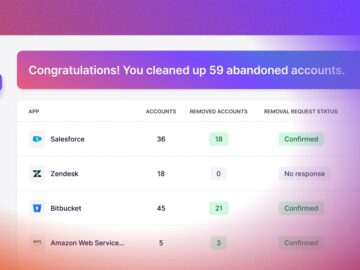
As the landscape of modern work changes, with its distributed teams and quickly evolving cloud-based technologies, maintaining access controls is…
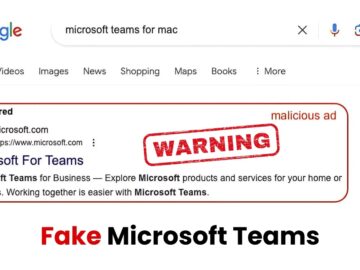
Hackers often mimic popular tools like Microsoft Teams to exploit people’s trust and familiarity with these applications. This strategy increases…
In June of this year, the Kaspersky cybersecurity firm, led by Eugene Kaspersky, was banned by the Joe Biden administration,…
Police Digital Service (PDS) CEO Ian Bell is no longer a director of the company, two weeks after it emerged…
MarineMax, self-described as the world’s largest recreational boat and yacht retailer, is notifying over 123,000 individuals whose personal information was stolen…
The cybersecurity landscape is a battlefield, but the biggest threats don’t always come from external hackers. As a seasoned warrior…
Void Banshee exploits CVE-2024-38112 zero-day to spread malware Pierluigi Paganini July 17, 2024 Void Banshee APT group exploited the Windows…
MarineMax, self-described as the world’s largest recreational boat and yacht retailer, is notifying over 123,000 individuals whose personal information was stolen…
The Labour government has announced its legislative agenda for the new Parliament, with the King’s Speech outlining bills covering cyber…