Police Digital Service (PDS) CEO Ian Bell is no longer a director of the company, two weeks after it emerged…
MarineMax, self-described as the world’s largest recreational boat and yacht retailer, is notifying over 123,000 individuals whose personal information was stolen…
The cybersecurity landscape is a battlefield, but the biggest threats don’t always come from external hackers. As a seasoned warrior…
Void Banshee exploits CVE-2024-38112 zero-day to spread malware Pierluigi Paganini July 17, 2024 Void Banshee APT group exploited the Windows…
MarineMax, self-described as the world’s largest recreational boat and yacht retailer, is notifying over 123,000 individuals whose personal information was stolen…
The Labour government has announced its legislative agenda for the new Parliament, with the King’s Speech outlining bills covering cyber…
Cybersecurity firm Resonance Security has rolled out ‘Harmony’, a new asset monitoring tool to guard Web2 and Web3 apps from…
Quick take: Harmony is the fourth cybersecurity application Resonance developed to address the disconnect in cybersecurity practices. Harmony captures continuous…
To block, or not to block – this question is one that many cybersecurity teams are grappling with as they…
Life360, a popular family location tracker app, suffered a data breach affecting 443,000 users. Personal details, including first names and…
17 Jul Cybercrime Magazine Will Be At DEF CON 32 In Las Vegas Posted at 09:03h in Blogs by Di…
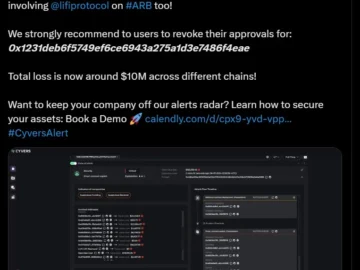
Just two years after patching a similar exploit, cross-chain Decentralized Finance (DeFi) protocol Li.Fi has been hit again by hackers,…