Killer Ultra malware has been found to be targeting endpoint detection and response (EDR) tools from Symantec, Microsoft, and Sentinel…
The second quarter of 2024 witnessed significant developments in the ransomware landscape, characterized by challenges and adaptations within the RaaS…
Atlassian, a leading provider of collaboration and productivity software, has released critical security updates addressing multiple high-severity vulnerabilities in its…
The Australian Signals Directorate has partnered with Amazon, the American technology giant, to establish a highly secure data center aimed…
Jul 17, 2024NewsroomCybercrime / Ransomware The infamous cybercrime group known as Scattered Spider has incorporated ransomware strains such as RansomHub…
The Octo Tempest group adds RansomHub and Qilin ransomware to its arsenal Pierluigi Paganini July 17, 2024 Microsoft said that…
Hackers often target internal communications tools to obtain confidential information like employee records, business plans, and proprietary technologies. With these…
As Paris gears up to host the 2024 Olympic Games, the city and its organizers face a monumental task not…
In a heartfelt letter titled “To our Lovely you,” Kaspersky Lab, the Russian cybersecurity firm, has announced its departure from…
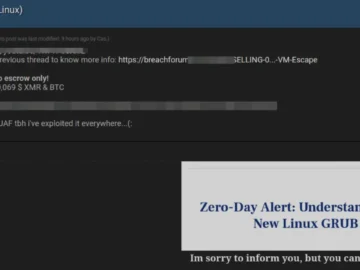
A new threat has emerged concerning the security of VirtualBox virtual machines (VMs). A threat actor known as Cas has…
Jul 17, 2024NewsroomVulnerability / Data Security Threat actors are actively exploiting a recently disclosed critical security flaw impacting Apache HugeGraph-Server…
Spyware presents a serious threat by infiltrating devices, accessing sensitive data, and transmitting it without consent. This form of attack…