The Department of Health and Aged Care has contracted Accenture to supply contractors into a large-scale digital transformation program underway…
The FBI announced on Monday that it seized the servers and websites of the Radar/Dispossessor ransomware operation following a joint…
US electric utilities sounded bullish on demand from data centres powering the artificial intelligence boom after striking several supply deals…
In a coordinated international takedown, the FBI, in collaboration with law enforcement agencies across the globe, has dismantled the infrastructure…
Australian’s Evolution Mining said it became aware of a cyber attack last week, amid a spate of similar incidents that…
South Korea’s ruling party, People Power Party (PPP), claims that North Korean hackers have stolen crucial information about K2 tanks,…
Over 100 Ukrainian state and local government computers have been compromised with MeshAgent malware in a phishing campaign leveraging trust…
Evolution Mining has informed that it has been targeted by a ransomware attack on August 8, 2024, which impacted its…
Microsoft announced that the Paint 3D graphics app will be discontinued later this year and removed from the Microsoft Store…
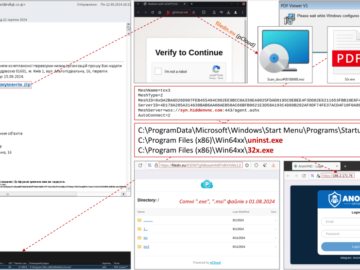
Attackers impersonating the Security Service of Ukraine (SSU) have used malicious spam emails to target and compromise systems belonging to…
A FreeBSD flaw could allow remote code execution, patch it now! Pierluigi Paganini August 12, 2024 FreeBSD Project maintainers addressed…
Microsoft has shared a temporary fix for a known issue preventing Microsoft 365 customers from signing in or adding Gmail…