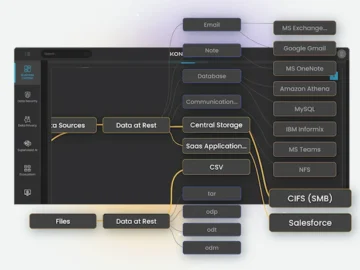
1touch.io unveils Kontxtual, an AI-driven data platform engineered for the AI era. Built to accelerate enterprise innovation without compromising control,…
Marks And Spencer Group Plc (M&S) has reported a dramatic decline in its first-half profit, largely from the financial impact…
Cl0p, a prominent ransomware group operating since early 2019, has emerged as one of the most dangerous threats in the…
Authorities across nine countries executed a coordinated crackdown on one of the largest credit card fraud networks ever dismantled. Operation…
In this Help Net Security video, Peled Eldan, Head of Research at XM Cyber, explains the hidden risks of shadow…
A sophisticated Remote Access Trojan (RAT) is actively targeting North Korean Human Rights Defenders (HRDs) through a campaign leveraging stolen…
Bitdefender announced Bitdefender GravityZone Security Data Lake and Data Lake for Managed Detection and Response (MDR), solutions that help organizations…
Nov 06, 2025Ravie LakshmananMalware / Network Security The threat actor known as Curly COMrades has been observed exploiting virtualization technologies…
Banks across Asia are pouring billions into artificial intelligence systems to detect fraud, but regulators and analysts say the region…
The cybersecurity landscape stands at a critical inflection point as organizations prepare for unprecedented challenges in 2026. Google Cloud researchers…
Hyundai AutoEver America, LLC has formally confirmed a significant data breach that compromised sensitive customer information. The automotive software provider…
When you ask a large language model to summarize a policy or write code, you probably assume it will behave…